Benefits of Two Factor Authentication: Why Good Passwords Aren’t Good Enough
What is Two Factor Authentication?
The most common form of multi-factor authentication is two-factor authentication (2FA). We will get into the benefits of two factor authentication after you learn what it is. As its name suggests, two-factor authentication combines two different methods to confirm a user’s identity.
In order of security levels, 2FA will ask users for validation by asking for proof of:
- Something they know – a PIN, address or answers to secret questions
- Something they have – a card, email, FOB, iPhone, App or USB drive
- Something they are – a fingerprint, iris scan, or voice
A common example, in order to use a credit card online or over the phone, you may have to scan the card (#2 something they have) and enter a PIN (debit) or a billing zip code (credit) (#1 something they know). Adding a code sent to your email or mobile phone (#2 something they have) to authorize the purchase adds another level of security.
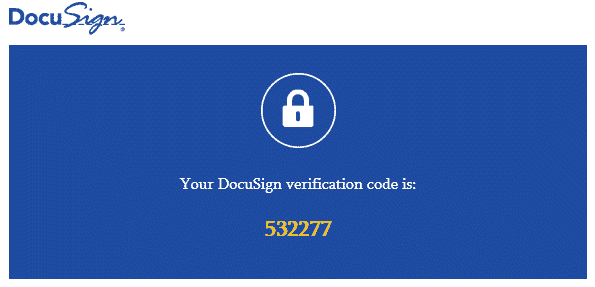
Good passwords aren’t good enough
Most websites, subscriptions, and/or apps only require a username and a password. While this is extremely convenient, it creates a data security risk. In a prior article, we covered the importance of good passwords in depth and why small business owners MUST know their logins, but good passwords and good data security practices aren’t always enough.
- You may give your password to someone, and they share it.
- You may reuse your passwords, so when one site is hacked, criminals try using those same credentials on bank account and investment sites.
Once someone is in your account, you’ve lost control. It’s like letting a burglar in the house. You can lock the doors after they leave, but it’s too late – they already have all your sensitive data.

Benefits of two factor authentication security levels
The more data security factors you have in place, the more protection you have. But the quality of the factors themselves are also important. Criminals can easily find out your mother’s maiden name. Getting your fingerprint is much harder.
The most common two-factor authentication step right now is to send a code to your mobile phone via email or text. You’ll receive an alert if someone TRIES to get into your account. While this process takes another 15 seconds to validate your credentials, it should be your default setting for:
- Anywhere you have superuser or admin credentials
- Bank, financial and investment sites
- Sites that store sensitive client information
- Email logins. Once criminals get into your inbox, they often find a treasure trove
Benefits of two factor authentication will majorly out-weigh the minor inconvenience of using two devices.
Managing two factor authentication
Your IT Policies and Procedures should require employees to use two-factor authentication for all websites and/or apps that contain sensitive or financial data. If you manage a website for your clients, a software development company (like us) can help you offer this added layer of security for your users.
Another idea is to send links to files instead of attaching files directly to emails. That way the addressee must be credentialed on the system before they can view the file. This will also help your computer files stay organized!
What is two factor authentication?
Two-factor authentication is an extra layer of security to prevent someone from logging in, even if they have the password. You will have to verify your identity with a 6 digit code sent to your phone every time you log in. This makes sure that only YOU can log in to your account.
How do you set up 2FA?
Most sites include 2 factor authentication somewhere in their settings. It’s going to vary for each site, but check under settings and security to enable 2FA.
Can two factor authentication be hacked?
Hackers usually don’t have access to your login information and your phone messages. Two-factor authentication is extremely reliable in preventing attacks from hackers.